During my study for VCAP-DTA exam I hit the topic of SSL certificate management, so I decided in order to practice it to generate a SSL certificate for my Lab’s View Security Server and get a proper signed SSL certificate for it.
On your VMware Horizon View Security server open a command prompt to the following path: C:\Program Files\VMware\VMware View\Server\jre\bin
Run the following command to generate Keypair for your SSL certificate, this should be 2048 bit length and using password “secret”, the format of stored keystore is JKS:
keytool -genkeypair -keyalg “RSA” -keysize 2048 -keystore keys.jks -storepass secret
Now as we generated the Keypair, it’s time to create the certificate request by running the following command:
keytool -certreq -file certificate.csr -keystore keys.jks -storepass secret
The SSL certificate request file (certificate.csr) is ready to be sent to CA for signing it.
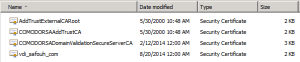
In my case I got from my CA provider the following four files:
AddTrustExternalCARoot –> External Root CA
COMODORSAAddTrustCA –> Provider Intermediate Root CA
COMODORSADomainValidationSecureServerCA –> Provider Domain Validation Server CA
vdi_safouh_com –> My Domain SSL signed certificate
So you need to start importing the External Root CA at first by running the following command:
keytool -importcert -keystore keys.jks -storepass secret -alias rootCA -file AddTrustExternalCARoot.crt
where Keystore file name is “keys.jks” and it’s password “secret”.
Then import the next level certificate which is Provider Intermediate Root CA by running the following command:
keytool -importcert -keystore keys.jks -storepass secret -trustcacerts -alias intermediateCA -file COMODORSAAddTrustCA.crt
Now we need to import the next level in CA’s validation chain by running the following command:
keytool -importcert -keystore keys.jks -storepass secret -trustcacerts -alias intermediateCA -file COMODORSADomainValidationSecureServerCA.crt
Finally we will import our domain signed SSL certificate, which is in my case “vdi.safouh.com” by running the following command:
keytool -importcert -keystore keys.jks -storepass secret -keyalg “RSA” -trustcacerts -file vdi_safouh_com .crt
Now copy “keys.jks” file to the following location: C:\Program Files\VMware\VMware View\Server\sslgateway\conf
Create the following file: locked.properties at above location, this configuration file contains the SSL configurations details, and add the following line to it: (only bold ones)
keyfile=keys.jks [this is the Keystore file name which we copied to here]
keypass=secret [Keystore password]
storetype=jks [Keystore type]
Save the file and restart the view Security Server.
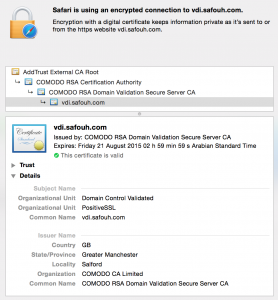
Now you should have a valid SSL Certificate for your Security Server … something like the following:
You can see the SSL CA chain in addition to other details … by the way, that SSL certificate costed me only $9,- per year 🙂